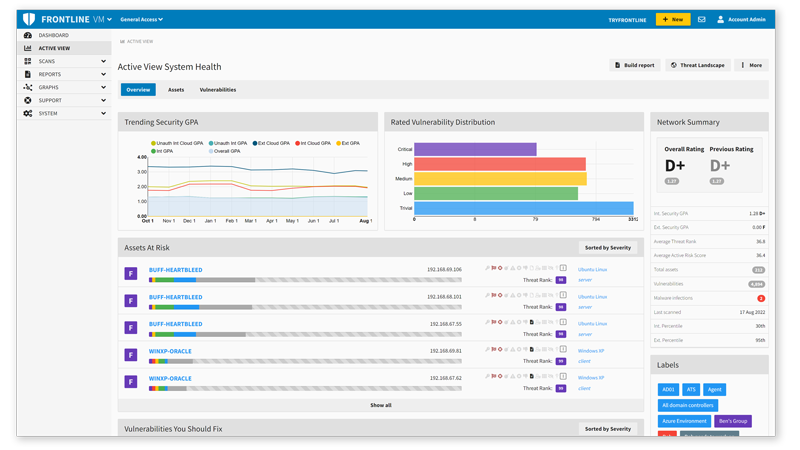
Threat Landscape
Threat Landscape leverages threat intelligence to help you understand the truly exploitable vulnerabilities that exist in your environment, allowing you to create a remediation strategy that is most productive for your organization's unique risk posture.
Threat Landscape™ shines a light on the truly critical vulnerabilities.
Keeping informed of threat intelligence, such as the most-used exploits, popular crimeware and exploit kits, and threat trends, and then distilling and correlating the information to your existing vulnerability management framework is time consuming and can overwhelm the most seasoned cybersecurity veterans.
Narrow your team’s focus to vulnerabilities that are exploitable in your organization’s environment.
Threat Analysis Pipeline
Threat Landscape is powered by Threat Analysis Pipeline (TAP) our proprietary machine learning model that aggregates daily threat intelligence feeds to correlate reported incidents with vulnerability exploitation. TAP combines common vulnerability metrics such as CVSS, CWE, and CPE with vulnerability exploitation data to rank threats and vulnerabilities and score your appetite for risk.
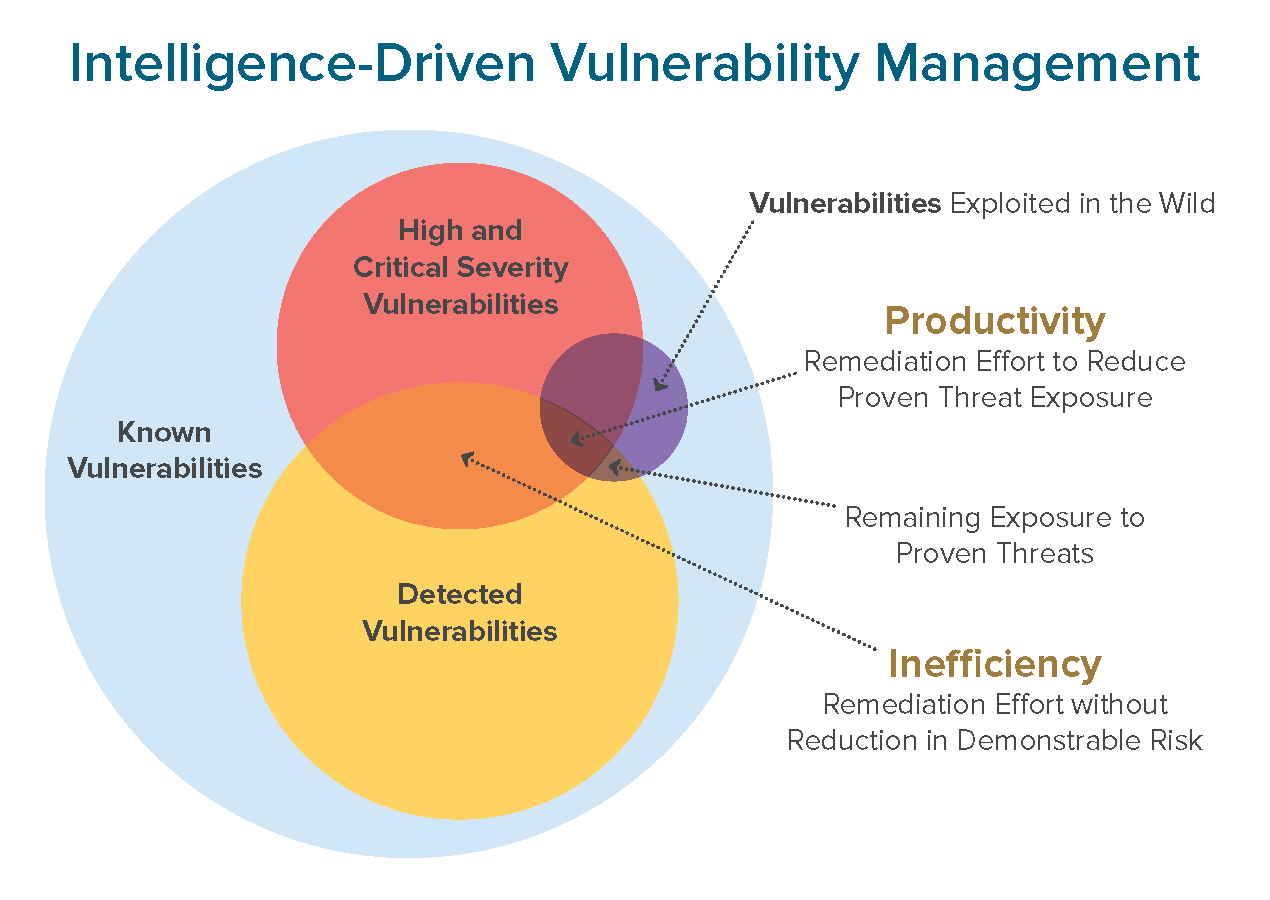
The result is an enriched data set to determine the likelihood of exploitability for each vulnerability, and the likelihood of weaponization of each exploit in the wild, as they relate to your environment.
Components of Threat Landscape
Threat Rank
Ranks the possibility of exploitation inside your network by identifying upcoming attack vectors yet to be realized in the wild. Using these models, organizations can stay ahead of attacker-weaponized vulnerabilities by resolving those most likely to be exploited.
Active Risk Score
Uses prebuilt or configurable risk profiles combining vulnerability severity, Threat Rank Score, asset exposure, and asset criticality to create and rate your organization’s risk appetite.
Measure your remediation efforts.
Empower your security operations center to analyze and report on trends and metrics for every asset and vulnerability in your Threat Landscape, and demonstrate targeted, measurable progress in securing your environment.
And, unlike competitors whose solutions have become commoditized or are just “add ons,” vulnerability and threat management is Digital Defense’s core focus. Our commitment to that purpose doesn’t end with a few patents. Digital Defense continues innovating to ensure the strength of that foundation never waivers—which is why more customers switch to Digital Defense every day.
Copyright © Fortra, LLC and its group of companies. Fortra®, the Fortra® logos, and other identified marks are proprietary trademarks of Fortra, LLC. | Privacy Policy | Cookie Policy | Sitemap